TryHackMe! Fowsniff CTF!
- Srivathsa Dhanvantri
- Aug 29, 2020
- 2 min read
TryHackMe is an online platform that teaches Cybersecurity through hands-on virtual labs. Whether you are an expert or beginner, learn through a virtual room structure to understand theoretical and practical security elements.

Fowsniff CTF is an easy room on TryHackMe for beginners to explore.
You have to first signup to join the room. There are few simple steps that you can follow in the Signup page. Next follow the steps in the Welcome room to configure the VPN connectivity.
I have connected to TryHackMe network using OpenVPN on Kali Linux. Once you connect, the access page will confirm the status by confirming your IP address and status.

Click on Deploy to start the target machine.

The IP address of the target is displayed.
Start Enumeration using nmap. The -sV option will do a service fingerprinting. - A is for aggressive scan. -p- will check all the ports.

From the scan result, it can be seen that port 80 is open and Apache server is running. Let us start checking each of these services listed in nmap scan result. Explore http service using a web browser.

There is a message on the web page that the website is down temporarily. It is always a good idea to check page source.

Looks like blackhat hackers have attacked the website and also taken over their twitter account. And the attackers may have uploaded sensitive information on twitter account. Please check the twitter account.

There is a post on twitter account by attackers that passwords have been posted on pastebin site. Check the pastebin site by following the link posted on twitter.
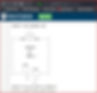
Note down all the credentials leaked on pastebin. From the nmap scan results we had seen that port 110 is also open and it is running pop3 service. Explore the pop3 service using netcat.

User seina's credentials worked and we are able to see the messages in the inbox. Check all the messages to find more information.

From the first email in the inbox, we can see a temporary password for SSH. Note it down. The SSH for siena or stone didn't work. Check the second message.

The second email is from baksteen. Probably another user. Try doing ssh using baksteen and the password from first email.

You are able to login as baksteen. Now run sudo -l command to check if the user has sudo permissions on this machine.
The sudo -l revealed that baksteen is not a sudo user. Get more information about the target machine using uname.

uname revealed the kernel version. Check if there are any exploits available on exploit-db for this kernel version to escalate privilege.

The google search result revealed there seems to be an exploit.

Download the exploit from the exploit db. Use gcc to compile the c program.

Start a python server on your Kali or whichever machine you are using for attacking.

Using wget command, download the complied code on the target machine. Give execution permissions to the downloaded exploit file using chmod command. Execute the exploit.

Note the root shell has been obtained. Check what's in root's home directory. By now you would have got all the answers for the questions in the TryHackMe room.
Congratulations!! you solved this room.

I hope this write-up was informative for you. Please leave a feedback. Thank you
-Srivathsa Dhanvantri